This report provides an analysis of significant security incidents and vulnerabilities within the cryptocurrency space during November 2024. Compared to the previous month, November saw a noticeable reduction in the frequency of major attacks, but the threat landscape remains highly active and sophisticated. The majority of these incidents continued to exploit weaknesses within smart contracts, underscoring the critical importance of developing and auditing secure, resilient contracts that cannot be easily manipulated by malicious actors.
One of the most alarming trends this month was the use of the DevCon 2024 event in Thailand as a foal point for cyberattacks - and physical attacks - targeting attendees who were likely cryptocurrency users. Malicious actors took advantage of the large gathering of developers, investors, and enthusiasts to deploy scams, including phishing attempts and social engineering attacks, with some victims suffering significant financial losses. Notably, a scam involved misleading users into registering for a fake Solana event, where participants were later targeted with fraudulent NFT minting emails. This highlights the importance of both on- and off- chain security, especially given attackers’ evolution of techniques to hack and scam cryptocurrency traders.
This report will examine the key vulnerabilities exploited during the month, the methods used by attackers, and provide an analysis of ongoing trends in crypto-related cybercrime. It aims to offer actionable insights and highlight the urgent need for the industry to improve security practices, such as user education and comprehensive due diligence, to prevent future attacks and mitigate the risks facing crypto users and platforms alike.
Key Incidents Overview
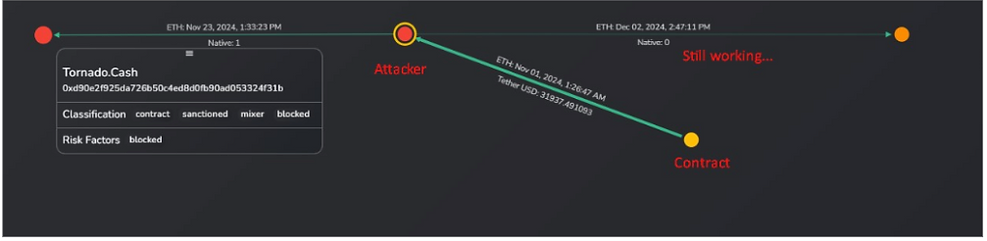
CyUSDT - November 1, 2024
Type: Exploit transaction in initcode
Description: A sanctioned address of Tornado Cash, the notorious virtual currency mixer, appears to have stolen $31,947.71 worth of cryptocurrency from an unsuspecting victim, exploiting a transaction using an initialisation in the code. NOMINIS Vue detected the transaction on Ethereum, as demonstrated below. A sanctioned address associated with Tornado Cash, the infamous virtual currency mixer, has reportedly stolen $31,947.71 worth of cyUSDT, a stablecoin renowned for trading within 10 basis points of its USD peg, making it a reliable store of value. The theft occurred through an exploited transaction leveraging malicious initialization code with exploitable logic designed for unauthorized actions. NOMINIS Vue identified this activity on Ethereum, as detailed below. The attacker remains active and at large.
Impact: $31,947.71
Coin31 - November 2, 2024
Type: Smart Contract vulnerability
Description: The Coin31 token was attacked, resulting in an almost $26k loss on the BSC mainnet. The attackers manipulated an unprotected and uninitialized function, setMaster, in the code, setting the master address to their own contract. This allowed the attacker to entirely drain the Coin31 token pool.
Impact: $25,926.85
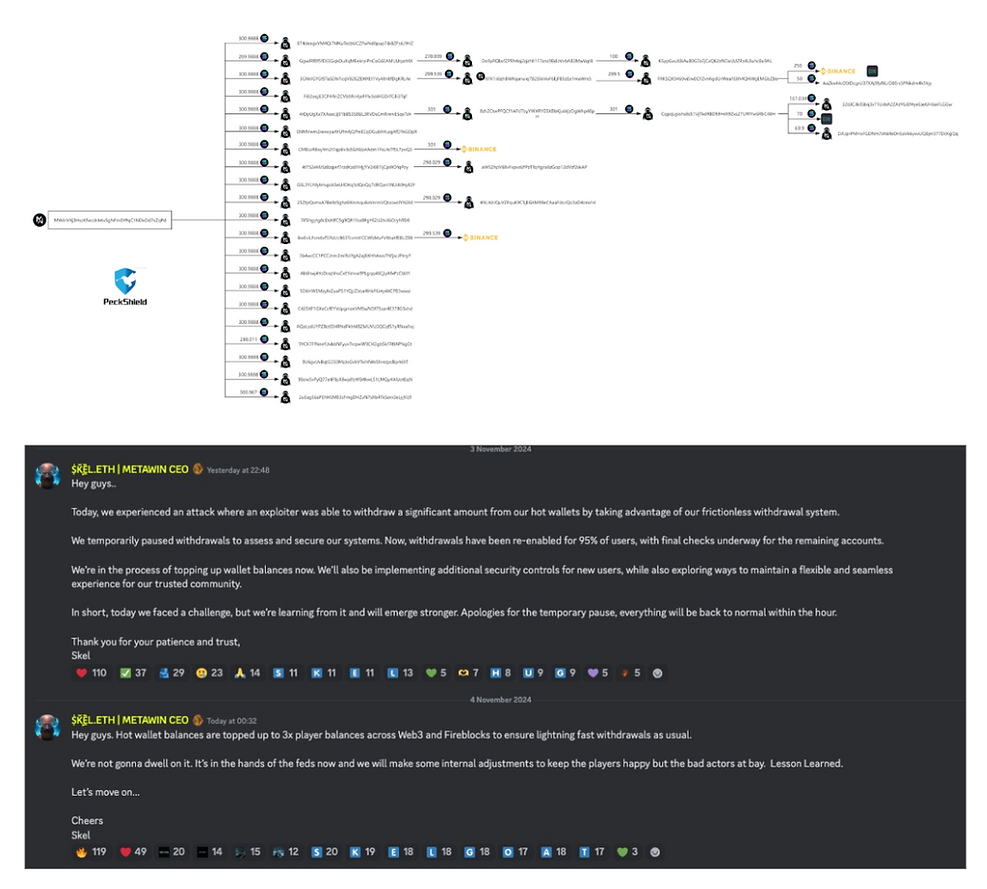
Metawin (Gambling platform) - November 4, 2024
Type: System Vulnerability
Description: Scam alert profile on X, PeckShieldAlert, reported that MetaWin, a gambling platform, was hacked, stealing the equivalent of $4 million from hot wallets. Coins that were stolen included Ethereum, Base and Solana. The hacker then transferred some of the funds over to Kucoin, HitBTC on Ethereum, Binance, and ChangeNow on Solana. The hack was performed by taking advantage of the ‘frictionless withdrawal system’ - though the lack of friction for withdrawals was designed for easy user experience, it highlights the difficult balance of ensuring an easy but also safe UX that is not susceptible to cyber threats.
Impact: $4,000,000
#BGM on #BSC - November 11, 2024
Type: Price Manipation attack
Description: On 11 November it was detected that there was an attack targeting BGM Token on the BNB Smart Chain. It was a price manipulation attack, ‘exploiting the reliance on the spot price’ .
Impact: $450,000
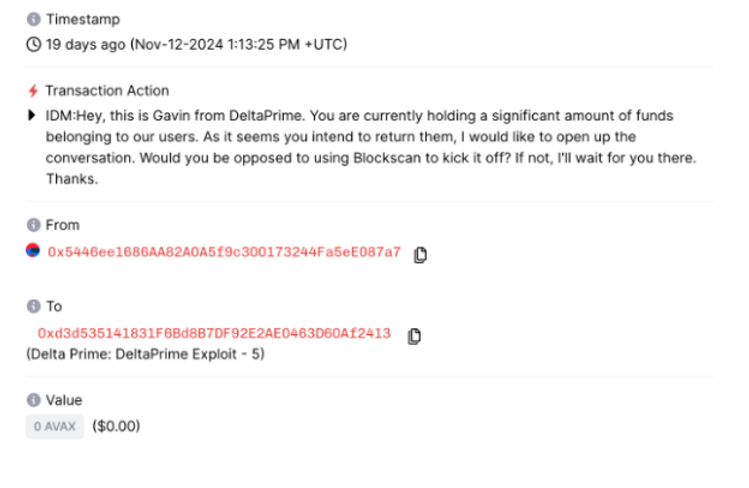
Delta Prime - November 11, 2024
Type: Infrastructure
Description: On November 11, Delta Prime recognised a large amount of funds had been taken from users and held by account ‘0xd3d535141831F6Bd8B7DF92E2AE0463D60Af2413’. Co-founder of DeltaPrime Gavin Hasselbaink sent an on-chain message via Snowtrace to the account, which did not receive a response. Following this, DeltaPrime turned to Twitter, where they sent they publicly addressed the attacker with their tweet ‘A message to the attacker’, asking for the attacker to make contact. Analysis suggests that the exploit was possible due to the lack of input validation in claiming rewards. This is in fact the second incident for the DeFi protocol, following a hack in September 2024 that led to a $6 million loss.
Impact: $4,800,000

Thala - November 15, 2024
Type: Security Vulnerability
Description: The Aptos-based DeFi project Thala recently suffered a security breach due to a vulnerability introduced in a recent update to its v1 farming contracts. This flaw enabled an attacker to exploit the system and withdraw liquidity pool tokens worth $25.5 million. In response, Thala quickly halted all affected contracts and froze its token assets, including $9 million in MOD and $2.5 million in THL. Working with other organizations, the team was able to identify the attacker and negotiate a $300,000 bounty, ultimately securing the full recovery of user assets.
Impact: $25,500,000
Polter Finance (Lending project) - November 17, 2024
Type: Smart Contract Vulnerability
Description: The lending project Polter Finance on Fantom was forced to halt operations after it suffered an attack that saw its Total Value Locked (TVL) plummet from about $9.7 million to just $60,000. This exploit appears to have stemmed from a smart contract vulnerability that was introduced just before the attack, enabling lending from the token ‘BOO’. The attacker exploited a vulnerability in the contract’s price calculations, allowing them to inflate the price of BOO and borrow more tokens than the collateral was worth. Polter Finance admitted following the attack that it failed to conduct a third-party audit of the smart contract, so the vulnerability was not identified during internal testing.
Impact: $8,700,000
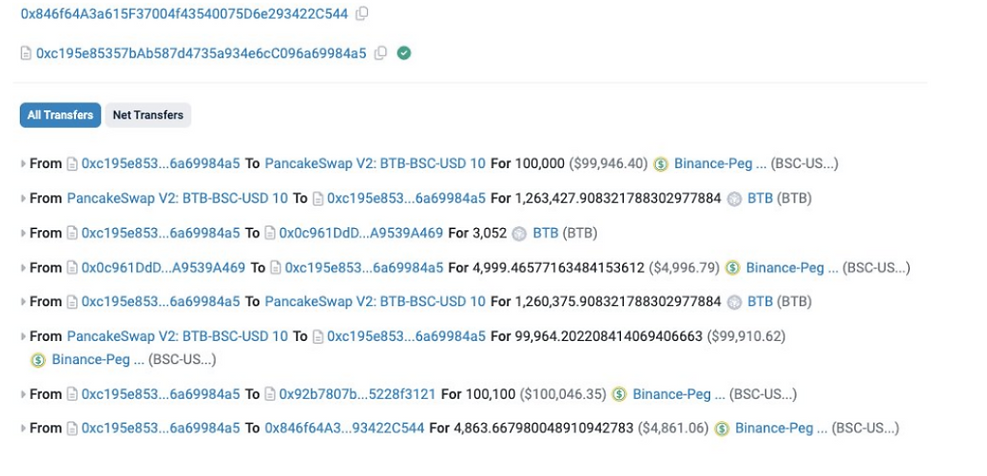
BTB Token - November 18, 2024
Type: Flash Loan Attack/ Smart Contract Vulnerability
Description: On November 18, 2024, the BTB token on the BNB Smart Chain (BSC) was exploited, resulting in a loss of around $5,000. The attacker used a flash loan to manipulate the BTB-BUSD price and exploited weaknesses in the contract's price oracle mechanism.
Impact: $5,000
ARC Token - November 18, 2024
Type: Compromised Private Key
Description: $749k of ARC tokens disappeared after the security of a private key was compromised on Arbitrum.
Impact: $749,000
Sweeper Token (SWEEPR) - November 22, 2024
Type: Contract Vulnerability
Description: The Sweepr Token (SWEEPR) on Ethereum has been suspected of an attack, resulted in about $14k in losses. Though there is not much detail known about the suspected attack, there is some information about the transaction hash and sender/ receiver addresses.
Impact: $14,000

https://etherscan.io/tx/0xec4e5e9b0bec380f8f6119756b9b13d6207c58bd2afbbcb876378d5baed73b9e
Matez (MATEZ) - November 22, 2024
Type: Contract vulnerability
Description: The Matez (MATEZ) on BSC is suspected to have been attacked, resulting in a loss of at least $80K.
Impact: $80,000

https://bscscan.com/tx/0x840b0dc64dbb91e8aba524f67189f639a0bc94ee9256c57d79083bb3fd46ec91
Akashalife (AK1111) - November 24, 2024
Type: Contract Vulnerability
Description: The Akashalife (AK1111) on BSC was suspected to have been attacked, resulting in a loss of approximately $31.5K.
Impact: $31,500
DCF Token - November 24, 2024
Type: Price manipulation
Description:An attacker targeted an unknown Degree Crypto Token (DCT) on BNB Smart Chain. The exploit leveraged a design flaw in the DarkCrypto foundation (DCF) token’s transfer mechanism, which included a forced investment feature. When DCF tokens were sent to the USDT-DCT liquidity pool, 5% of the transferred tokens were automatically swapped for USDT and added to the liquidity pool. This triggered a price swap in the USDT-DCT pool, which the attacker manipulated to inflate the price of DCT tokens. By exploiting this mechanism, the attacker executed profitable swaps, draining the pool and realizing significant financial gains.
Impact: $442,000
XT Crypto Exchange - November 28, 2024
Type: Potential security breach
Description: XT.com, a Seychelles-based crypto exchange, which handles over $3.4 billion in daily trading volume, experienced a suspected hack involving $1.7 million. Data suggested that In response, the exchange suspended all withdrawals of assets, but also insisted that the stolen funds were from its own reserves, not user accounts, so the security of users’ wallets were not breached.
Impact: $1,700,000
Major Crypto Incidents by type - November 2024
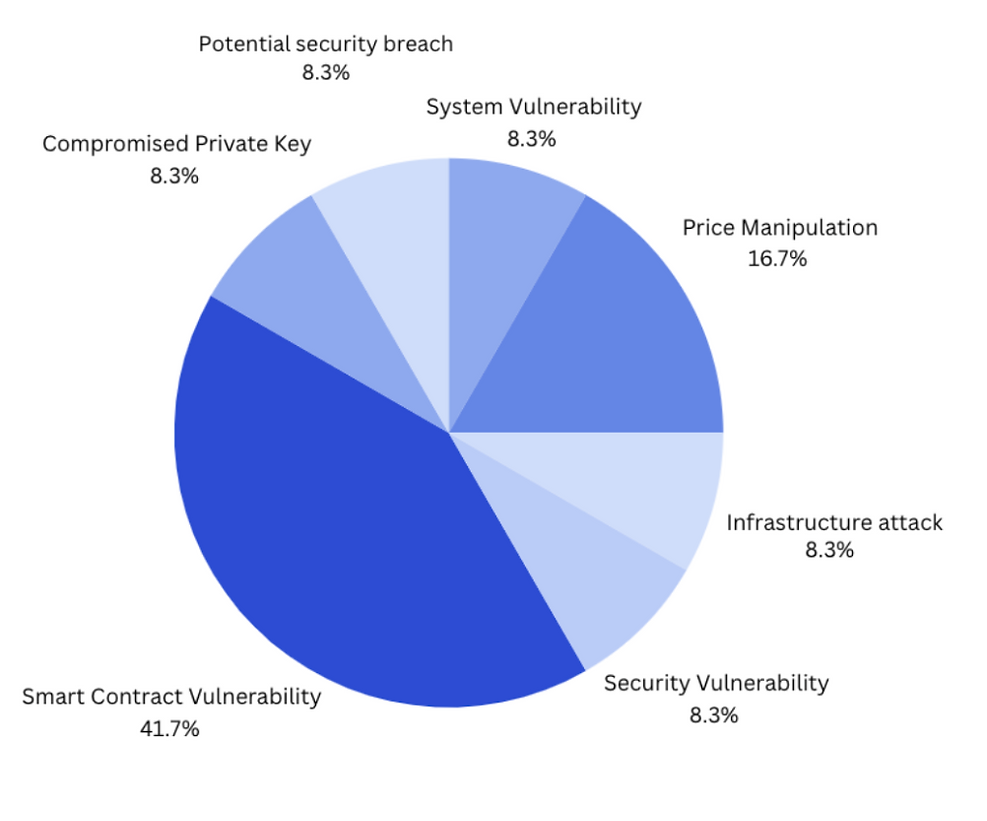
Major Crypto Incidents - November 2024

Individual use cases:
Among individual instances of crypto scams and hacks, one of the most significant attacks, leading to the loss of $20,000 worth of funds, is suspected to have been stolen via impersonation phishing websites. Additionally, numerous reported incidents were as a result of victims copying the wrong OKX or DEX wallet address, unfortunately as easily avoidable mistakes if users recognise the warning signs. These incidents amounted to losses of over $150 million. Copying the wrong address also took place as a result of an address poisoning transaction, which resulted in losses of $100k worth of USDT. Another of the most significant incidents included the draining of $4 million worth of crypto assets from wallets tied to crypto influencer JRNY, which appears to be due to a private key compromise.
Underscoring the intertwined nature of cryptocurrency and social media as a tool to promote the value of certain coins, Wiz Khalifa fell victim to a hack. Hackers pretending to be Khalifa used his X (formerly Twitter) account to encourage fans to invest in ‘WIZ’ , a coin he was allegedly involved in, however it was actually fictitious. The valuation of the coin reached a peak of $3.4 million just 15 minutes following Khalifa’s tweet, however the price severely dropped shortly afterwards. Data then showed two main wallets purchasing 155 million WIZ tokens, then selling the coins for a profit of $160,000.
Devcon incidents:
November 2024 saw the week-long global Ethereum developer conference DevCon 2024 take place, held in Thailand. While it is designed to be a place for international members of the Ethereum community; developers, researchers and enthusiasts, to come together and drive innovation, incidents occurred specifically targeting the attendees of the conference.
One incident reported involved robbers holding a Ukrainian man at knifepoint in a friend’s hotel room, bound him and forced him to transfer $500,000 in USDT to a specific wallet. Though he haggled with the robbers and ultimately only transferred $250,000 in USDT, the robbers have not been located. One has been identified as Armenian man Arman Grigoryan. It appears that with the event of DevCon taking place, it was known amongst assailants that many attendees own assets in cryptocurrency and make for interesting targets.
Additionally, reports of a scam campaign emerged in which DevCon attendees were targeted using a fake Eventbrite invite, used to distribute malicious NFT minting invites. While attendees thought they were registering for a specific event in the conference, it was recognised as a scam.

Key takeaways:
November’s trends:
In November 2024, the landscape of crypto security attacks demonstrated a noticeable decline in the frequency and severity of significant incidents compared to the previous month. However, the overall nature of these attacks continued to highlight persistent vulnerabilities, particularly around smart contracts and targeted social engineering tactics.
The frequency of major security breaches in the cryptocurrency space decreased in November, marking a shift from the more attack-heavy environment of October. While this could be attributed to various factors, including improved awareness and mitigation efforts, the overall trend indicates a potential reduction in large-scale exploitation of vulnerabilities.
Despite this, the industry remains vigilant, as fewer attacks can still have substantial financial and reputational consequences, as seen this month.
Smart contract vulnerabilities were the most common vector for cyberattacks during November, reinforcing a critical area of focus for the crypto community. These attacks leveraged flaws in the Open Source contract code, allowing attackers to exploit logic errors, underhanded contract interactions, or insufficient testing before deployment. This emphasizes the ongoing need for rigorous auditing and testing of smart contracts, as well as the development of more robust, secure coding standards. Vulnerabilities in decentralized finance (DeFi) protocols, often powered by smart contracts, were particularly targeted.
Attackers also adapted their strategies by taking advantage of major crypto events, notably Devcon 2024 held in Thailand. A notable scam involved attackers impersonating legitimate event registrations for a Solana-focused event, prompting users to register for a false event. This incident highlights the persistent threat of social engineering, particularly during high-profile industry events where many users are more susceptible to scams.
While the decline in overall attacks suggests that some preventative measures may be having an effect, the continued targeting of smart contracts and social engineering scams indicates that attackers are honing their focus on specific, highly exploitable weaknesses. The fact that events like Devcon 2024 are being used as vectors for phishing and social engineering attacks demonstrates the sophistication of modern attackers, who are clearly evolving and increasingly integrating both technical exploits and psychological manipulation to achieve their goals.
The persistence of smart contract vulnerabilities, despite growing awareness and advancements in auditing tools, suggests that the community must push for a greater emphasis on secure contract development and thorough testing. Similarly, the rising trend of scams surrounding major crypto events shows that even experienced users are not immune to targeted attacks, particularly when the attacks are wrapped in the guise of a legitimate, high-profile event.
As a result, crypto users and exchange platforms alike must double down on education around smart contract security and phishing prevention, as well as work to ensure that security protocols extend beyond just the digital realm into event security and personal precautions.






.png)